Google Calendar Spam
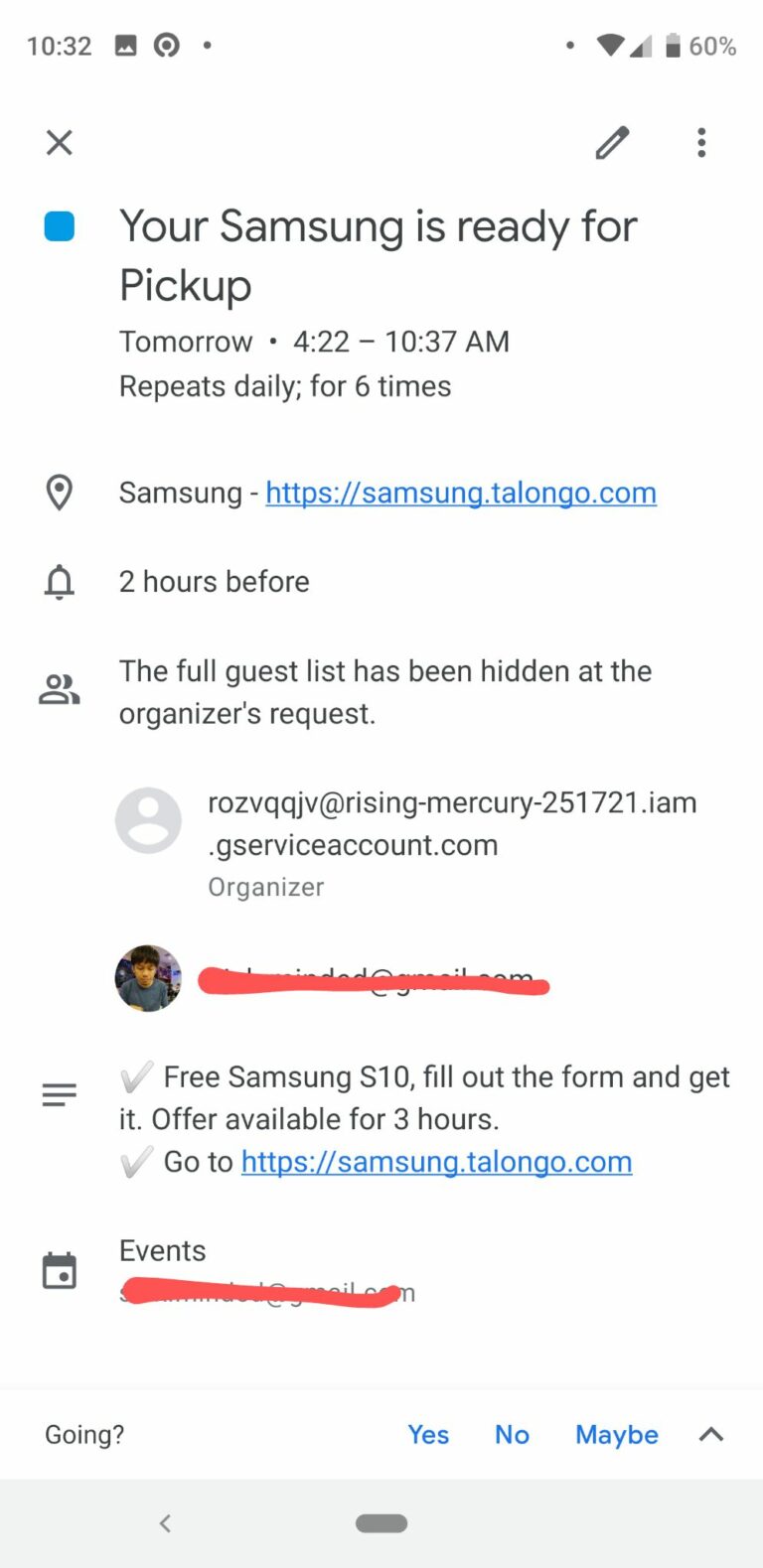
Some time ago @mubix tweeted about spam that entered Google Calendar, he felt he had never published his calendar, and did not find the e-mail associated with the purchase of iPhone XS Max (according to the tweet). When I saw…
Keamanan siber, sejak 2007.
Keamanan siber, sejak 2007.

Some time ago @mubix tweeted about spam that entered Google Calendar, he felt he had never published his calendar, and did not find the e-mail associated with the purchase of iPhone XS Max (according to the tweet). When I saw…

For the past few months, I have been preparing for the Advanced Windows Exploitation (AWE) training at one of Asia’s most popular hacker conferences, Black Hat Asia 2019. AWE is one of the training organized by Offensive Security LLC, a…
Zahir Accounting adalah software akuntansi yang sangat banyak digunakan oleh tingkatan SOHO (Small Office Home Office) di Indonesia. Selain harganya yang terjangkau, Zahir memiliki fitur yang lebih dari cukup untuk menyelesaikan pencatatan akuntansi yang tanggung, dalam arti mampu menyisir tingkat…
Some time ago while doing a pentest, we found a vulnerability in a file sharing web application named FileRun. This application allows us to access our files anywhere through self-hosted secure cloud storage, backup and sharing files for our photos,…
It’s been a while since the last post about exploitation on this blog. This time, we try to explain a stack based overflow on a software called Cyberlink LabelPrint. The software serves as a tool to assist in designing labels…
We discovered the vulnerability when we’re looking for alternate software in network monitoring. We know and we love Nagios, and so the Centreon, they provide a very nice interface of Nagios. Centreon provide nice features and ease of use when…
PC Media Antivirus (PCMAV) is an antivirus made by famous Indonesia computer magazine PCMedia . PCMAV is quite popular in 2006 since many virus creators in Indonesia actively spread a computer virus and infecting most computers in Indonesia. At that…
Trend Micro Control Manager prior to version 5.5 build 1823 (English and Japanese version) and version 6 build 1449 (English version only) are susceptible to SQL Injection. The application does not properly filter user-supplied input. The successful exploitation of this…
Overview webERP is a mature open-source ERP system providing best practice, multi-user business administration and accounting tools over the web. The vulnerability sits in the WO (work order) parameter, file WorkOrderEntry.php in the Manufacturing menu. Lack of input validation of…
Trend Micro InterScan Messaging Security Suite is vulnerable to Cross-site Scripting and Cross-site Request Forgery. Proof of Concept The vulnerabilities POC are as follow: Cross-site Scripting (CVE-2012-2995) (CWE-79) Persistent/Stored XSS Non-persistent/Reflected XSS Cross-Site Request Forgery (CVE-2012-2996) (CWE-352) Solution Currently, we…