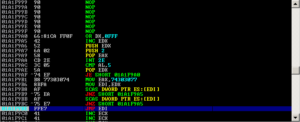
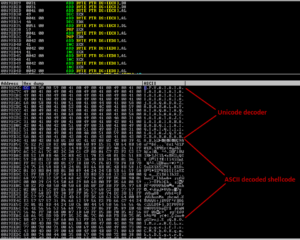
Trend Micro Control Manager prior to version 5.5 build 1823 (English and Japanese version) and version 6 build 1449 (English version only) are susceptible to SQL Injection. The application does not properly filter user-supplied input. The successful exploitation of this vulnerability could potentially result in arbitrary SQL command input to the back-end database, such as execute SQL command to upload and execute arbitrary code against the target system.
The vulnerable parameter is ‘id’ parameter in the GET request for AdHocQuery_Processor.aspx page. According to Trend Micro Control Manager help page, an Ad Hoc Query is a direct request to the Control Manager database for information. The query uses data views to narrow the request and improve performance. After specifying the data view, users can further narrow their search by specifying filtering criteria for the request.
Version Affected
Trend Micro Control Manager 5.5 prior to 5.5.0.1823 (English and Japanese version)
Trend Micro Control Manager 6 prior to 6.0.0.1449 (English version)
Impact
An attacker with access to the Trend Micro Control Manager web interface can conduct a SQL injection attack, which could be used to result in information leakage, arbitrary code execution and/or denial of service.
Solution
The vendor has stated that these vulnerabilities have been addressed in Trend Micro Control Manager version 5.5 and 6.0 critical patches.
Critical patch available for SQL injection attacks in Control Manager (TMCM)
http://esupport.trendmicro.com/solution/en-us/1061043.aspx
Control Manager 6 – Product Patch
http://downloadcenter.trendmicro.com/index.php?clk=tbl&clkval=4202 – fragment-4248
Control Manager 5.5 – Product Patch
http://downloadcenter.trendmicro.com/index.php?clk=tbl&clkval=1763 – fragment-1845
Trend Micro Control Manager 5.5 – Patch (Japanese only)
http://downloadcenter.trendmicro.com/index.php?regs=jp&clk=tbl&clkval=3432 – fragment-3462
Proof of Concept
https://github.com/modpr0be/exploit-dev/blob/master/exploit-repo/controlmanager-trendmicro/poc.py
References
JVN#42014489 – http://jvn.jp/en/jp/JVN42014489/index.html
VU#950795 – http://www.kb.cert.org/vuls/id/950795