ScriptFTP client is vulnerable against remote buffer overflow vulnerability. The condition is triggered while processing LIST FTP command with excessive length.
The vulnerability is confirmed in version 3.3. Other version may also be affected.
Software Description
ScriptFTP is a FTP client designed to automate file transfers. It follows the commands written on a text file (also called script file) and makes the uploads or downloads automatically. Writing the script file is very easy, take a look at the script samples section.
Crash/Exploit Information
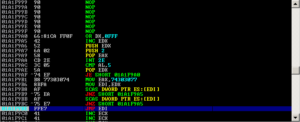
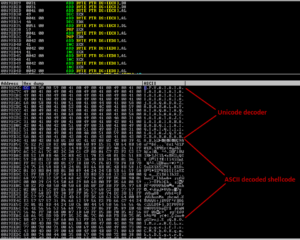
ScriptFTP follows the commands written on a text file (also called script file). Specifically, processing ScriptFTP with text file/script file contains command GETLIST or GETFILE of 3000 or more bytes of data may trigger an exception within the client, causing it to crash and lead us to stack overflow.
Proof of Concept
See the POC here and the script to generate ScriptFTP script here. Or if you were too lazy to generate the script, I already prepared it for you, just change the IP address.
Fix and Update
Vendor contacted and responded immediately after our first contact. They are planning to major rewrite but until now, no further info received from them. Do not connect to untrusted FTP server. Fix or update is not available yet, we will update this post if the vendor fix the bug.
Vendor Contact Log:
01/21/2011: Bug found
01/22/2011: Vendor contacted
01/24/2011: Vendor replied
03/07/2011: Update status to vendor
04/06/2011: Vendor received POC
05/17/2011: No further info, 1st reminder sent.
09/11/2011: No further info, 2nd reminder sent.
09/20/2011: No response, advisory released.